Colossus, the revolution in code breaking
Heath Robinson worked well enough to show that Max Newman's concept was correct. Newman then went to Dollis Hill where he was put in touch with Tommy Flowers, the brilliant Post Office electronics engineer. Flowers went on to design and build
Colossus to meet Max Newman's requirements for a machine to speed up the breaking of the Lorenz cipher. Tommy Flowers' major contribution was to propose that the wheel patterns be generated electronically in ring circuits thus doing away with one paper tape and completely eliminating the synchronisation problem.
This required a vast number of electronic valves but Tommy Flowers was confident it could be made to work. He had, before the war, designed Post Office repeaters using valves. He knew that valves were reliable provided that they were never switched on and off. Nobody else believed him!
 | Colossus design started in March 1943. By December 1943 all the various circuits were working and the 1,500 valve Mark 1 Colossus was dismantled, shipped up to Bletchley Park, and assembled in F Block over Christmas 1943. The Mark 1 was operational in January 1944 and successful on its first test against a real enciphered message tape. This is a 1945 photograph of a Mk II Colossus. No pictures of the Mk I have been found, but the Mk I did not have the large switch panel rack with the sloping plug panel on its front and only had a sigle bedstead frame, like Heath Robinson. |
The Colossus Computer
Each of the ten Colossi occupied a large room in F Block or H Block in Bletchley Park.
 | The racks were 90 inches, (2.3m), high of varying widths. There were eight racks arranged in two bays about 16ft (5.5m) long plus the paper tape reader and tape handler (known as the bedstead). The front bay of racks, spaced 5ft (1.6m) from the rear bay, comprised from right to left, the J rack holding the master control panel, the plugboard some cathode followers and the AND gates. |
Next came the K rack which contained the very large main switch panel together with the very distinctive sloping panel at the front which was a duplicate patch panel for the thyratron rings. Next came the S rack which held the relays used for buffering counter output and making up the typewriter drive logic. The left hand rack at the front was the C rack which held the counter control logic on the front and the decade counters on the back.
The rear bay of Colossus contained four racks, the R rack holding the staticiser and delta boards for the paper tape reader output and the K and S-wheel thyratron ring outputs, the M rack for the M-wheel staticisers and S-wheel motion logic. The very large W rack held, on one side all the thyratrons making up the wheel rings, 501 in all, and on the other side the 12 thyratron ring control panels. Also on the W rack were the link boards for the wheel patterns and the uniselectors for setting wheel start positions. The end rack of the back bay held the power packs. These were 50 volt Westat units stacked up in series to give +200 volts to -150 volts. The total power consumption was about 5 Kilowatts most of which was to the heaters of the valves.
The circuit layout was all surface mounting on metal plates bolted to the racks. The valve holders were surface mounting with tag strips for the components. This form of construction had much to commend it, firstly both sides of a rack could be used, secondly wiring and maintenance were very easy and lastly cooling of the valves was expedited by them being horizontal.
How Colossus worked
Colossus read teleprinter characters, in the international Baudot code, at 5,000 characters per second from a paper tape. These characters were usually the intercepted cipher text which had been transmitted by radio. The paper tape was joined into a loop with special punched holes at the beginning and end of the text. The broad principle of Colossus was to count throughout the length of the text the number of times that some complicated Boolean function between the text and the generated wheel patterns had either a true or false result. At the end of text the count left on the counter circuits was dumped onto relays before being printed on the typewriter during the next read through the text, an early form of double buffering.
Colossus had two cycles of operation. The first one was controlled by the optical reading of the sprocket holes punched between tracks 2 and 3 on the paper tape. The sprocket signal was standardised to 40 microseconds wide. The optical data from the paper tape was sampled on the back edge of the standardised sprocket pulse as was the outputs from the rings of thyratrons representing the Lorenz wheel patterns. The result of the logical calculation was sampled on the leading edge for feeding into the counter circuits.
The second cycle of operations occurred at the beginning and end of the text punched onto the paper tape. The paper tape was joined into a loop and special holes were punched just before the start of text between channels three and four (called the start ) and just after the end of text between channels four and five (called the stop). This long cycle of operations began with the electrical signal from the photocell reading the stop hole on the tape. This stop pulse set a bistable circuit which stayed set until the optical signal from the start hole was read. The setting of this bistable thus lasted for the duration of the blank tape where the text was joined into a loop, typically about 100 millisec.
The first operation after the stop pulse was to release any settings on the relays from the previous count. Next the new count was read onto the relays. Then the counters and the thyratron rings were cleared and then the thyratron rings were struck at the next start point to be tried. When the bistable was reset by the start pulse, sprocket pulses were released to precess the thyratron rings, to sample the data read from the paper tape and to sample the calculation output to go to the counters.
The various components of Colossus were the optical reader system, the master control panel, the thyratron rings and their driver circuits, the optical data staticisors and delta calculators, the shift registers, the logic gates, the counters and their control circuits, the span counters, the relay buffer store and printer logic.
The optical reader system
In order to break the Lorenz codes in a reasonable time the cipher text had to be repeatedly scanned at very high speed. This meant at least 5,000 characters per second and in the 1942 this implied hard vacuum photocells to optically read the holes in the paper tape. The smallest photocells available were some developed for proximity fuses in anti aircraft shells. Six of these in a row meant an optical projection system to enlarge the image of the paper tape about 10 times. Dr Arnold Lynch designed the paper tape reader and used slits cut into black card to form a mask in front of the photocells. The output from the data channels went to the staticiser and delta circuits.
The master control panel
This was where the start and stop pulses from the optical reader set and reset the bistable. Monostable delay circuits generated the voltage waveforms for releasing the relays, for staticising the counters, for resetting the counters and thyratron rings, and for striking the rings. Gate circuits controlled the flow of sprocket pulses.
The thyratron rings and their driver circuits
These circuits were the most complex on Colossus.
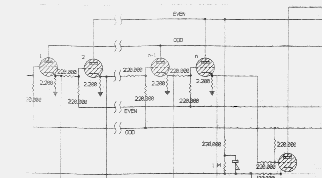 | Thyratrons are gas-filled triodes which strike a discharge arc between anode and cathode when the grid voltage is raised to allow electrons to flow. This discharge when struck continues quite independent of the grid voltage. Thus the thyratron acts as a one-bit store. It can only be switched off by driving both the anode and the grid negative with respect to the cathode. |
To construct a shift register with thyratrons requires that the striking of the next thyratron in the ring also quenches the previous thyratron. This leads to a biphase circuit with anodes of alternate thyratrons connected together and the grid voltage partially biased by the cathode voltage of the previous thyratron. The complication arises when a Lorenz wheel contains an odd number of setting lugs. The thyratron ring controller for this requires a complete set of circuits to handle just the odd thyratron in order to get back to the biphase circuits for the rest of the ring.
The thyratrons in a ring conduct sequentially stepped round by the sprocket pulses. Each thyratron cathode is brought out to a patch panel which allows the cathode pulse to be connected to a common output line when a link is plugged into the patchboard. Thus as the ring precesses round a sequence of pulses appears on the common output line. By selecting the link positions this sequence can replicate the mechanical lugs set on the Lorenz wheel. Alongside the patch panel is a Uniselector which selects the thyratron cathode to which the ring strike pulse goes. This is the start position of the ring when sprocket pulses come in at the start of text. The common line output went to the staticiser and delta circuits.
The staticisors and delta circuits
These circuits take the raw signals from the paper tape reader and the thyratron rings, sample them on the back edge of the clock pulse and set them to standard voltages of ± 80 v. Also on these boards are circuits giving a delay of one clock pulse. This is achieved with integrator capacitors which "hold" the previous data signal for long enough for it to be sampled on the next sprocket pulse. This delayed signal is available as an output but also on the board is an adder circuit which produces the delta signal, i.e. a 'one' when current data is different from previous, and a 'zero' when current equals previous.
The shift registers
These are the same circuits used as used on the delta boards, just integrators sampled on the next sprocket pulse.
Up to 5 shift elements could be connected in cascade giving a 5 bit shift register. This is thought to be the first recorded design or use of a shift register. Some of the computational algorithms used this window on previous data to improve the cross-correlation measurement.
The logic gates
Colossus was provided with AND, OR and XOR gates which could be plugged together in any combination.
The counter and counter control circuits
The decade counter circuits were based on a pre-war design by Wynn- Williams. They used a divide by two circuit followed by a ring of five pentodes. Four decades were required for each of the five counters used and each control circuit covered four decades of counters. The inputs to the control circuits were the output from the logic gates, the sprocket pulse for strobing and the reset pulse from the master control panel. Also on the control panels were comparator circuits between the outputs of the decade counters and switches on another panel. These switches could be set to any number in the range 0 to 9999. The output of the comparator could be included in the logic calculations thus for instance suppressing printing of scores below a set value.
The span counters
These were the same design of counters and counter control circuits with switches on another panel which could be set in the range 0 to 9999. The purpose of the span counters was to be able to ignore sections of the cipher text which were corrupted, possibly due to fading radio signals. The comparator output was used to gate the sprocket pulses which went to the main counter controllers, cutting off these pulses stopped the sampling of the logic calculation and thus ignored the section of text covered by the span counters.
The relay buffer store and printer logic.
Latching relays held the ending count on the decade counters. The start positions of the thyratron rings and the count for the previous run through the text are clocked out sequentially on to the typewriter by the printer relay and uniselector logic.
Programming Colossus
Programming of the cross-correlation algorithm was achieved by a combination of telephone jack-plugs, cords and switches. The main plug panel was on the rack nearest to the paper tape reader. The direct and delta signals from the paper tape reader and the K-wheel thyratron rings were on this panel. The changeover from direct to delta could also be achieved by switches. Also on the main plug panel were the input and output sockets for the AND gates and the so called "Q" sockets which took the calculated output to the main switch panel on the next rack to the left. This very large switch panel allowed signals to be combined through further logic gates and the results switched to any of the five result counters. As an example take the simple double-delta algorithm as devised by Bill Tutte. This requires two wheels to be run simultaneously: so take K4 and K5. First the delta outputs from channel 5 of the paper tape reader is combined in an XOR gate with the delta output of the K5 thyratron ring. Then this result is XORed with the XOR output of delta channel 4 and the delta output of the K4 thyratron ring. This result is plugged to Q1 and on the switch panel Q1 is switched to counter 1. The output can be negated before being counted so that the count can represent either the number of times the double-delta calculation equals one, or the number of times it equals zero.
The end of Colossus
After VJ Day, suddenly it was all over. Eight of the ten Colossi were dismantled in Bletchley Park. Two went to Eastcote in North London and then to GCHQ at Cheltenham. These last two were dismantled in the 1960s and in 1960 all the wartime drawings of Colossus were burnt. Of course its very existence was kept secret.















 Figure 4: details of an Enigma rotor:
Figure 4: details of an Enigma rotor:






